Safeguarding your sales data

In the world of sales and Customer Relationship Management (CRM), the impact of data security on your company’s sales and marketing teams is a crucial topic. Let’s deep dive into what is data security, why is data security so important, what you can do to step-up your game, and what to look out for when aspiring to industry leading security standards.
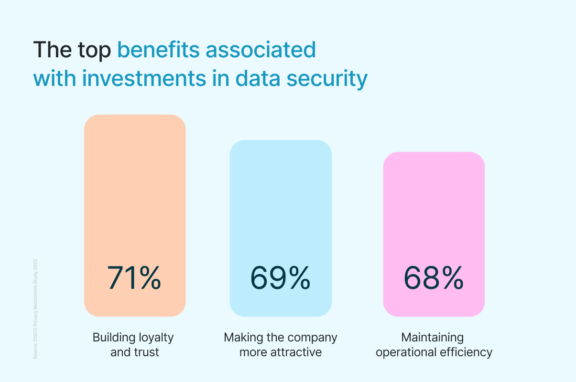
In sales, your customers are at the heart of your business. Their data is invaluable, representing a wealth of information about their needs, preferences, and interactions with your company. Customer records, past interactions, and deal status form the lifeline of your sales and marketing efforts. Implementing CIAM solutions for protecting personal data and protecting data in the cloud becomes paramount, not only for compliance but also for the success of your business. This is something we really need to reiterate. Data security and protection don’t only exist for you to be compliant for the sake of it – there are some real tangible benefits of having industry leading security standards. Besides, if you are serious about growing your business, you have to be serious about exceeding the security standards that your current business operations necessitate. If you’re not doing it, somebody else will.
Why is data security so important, you may ask? Well, let’s consider the potential consequences of a data breach. Beyond the regulatory fines and legal complications, a breach can severely damage your company’s reputation and erode the trust your customers have placed in you. In a hyper-connected digital world, where news spreads rapidly, trust is the currency that can make or break your business. A user can trust a brand when they have proven to handle and process data in a secure manner. This means following the best practices, using the most secure tools, and ensuring that the whole team is familiar with your security policies.
Now, here is the secret: good data security practices can positively impact your sales performance. The answer lies in building a culture of security within your company. When your employees are aware of the importance of data protection and actively participate in maintaining security protocols, it creates an environment of trust and confidence. This, in turn, translates into better customer relationships, increased customer satisfaction, and ultimately, improved sales performance. And that’s without even mentioning the benefits of having a clean CRM full of accurate data and a sales team that knows exactly where to find the data they need to close this deal.
Another undoubtable reason why good security practices improve sales performance can be found in the simplicity of competition. Maintaining a reliable level of security can give you a significant competitive advantage. In an era where data breaches are all too common, customers are becoming increasingly cautious about whom they share their information with. By demonstrating a robust commitment to data security, you can differentiate your company from competitors and position yourself as a trusted partner in their business endeavors.
But let’s not forget the elephant in the room: cyber security. The sales industry is not exempt from the ever-evolving threats posed by cybercriminals. Hackers constantly seek opportunities to exploit vulnerabilities, and CRM systems, with their treasure trove of valuable customer data, can be enticing targets. It is crucial to implement comprehensive security measures to safeguard your CRM and ensure that your customers’ information remains confidential and secure.
In the following chapters, we will delve deeper into specific security measures, best practices, and practical tips to fortify your data defenses. We will equip you with the knowledge and tools necessary to safeguard your sales data and protect your customers’ trust.
Remember, security is not just a checkbox to mark off—it is a mindset that should be ingrained in your company’s culture. By fostering a security-conscious environment, you pave the way for success, earning your customers’ loyalty and gaining a competitive edge in the sales industry.
How to bring your CRM data protection to an industry leading standard
Your CRM is, by nature, overflowing with Personally Identifiable Information (PII) of your clients and regulated info of many companies also. It also contains your full sales (and sometimes marketing) pipelines and if anything happens to this data, you’re out of the game – in other words, you risk losing your entire business activity. So what can we do to not just cover our backs, but leverage security into a tool for success?
1. Be mindful of access permissions:
One of the key elements of CRM advanced data protection is ensuring that access permissions are properly configured. Granting appropriate access levels to CRM administrators and users helps control who can view, edit, or delete sensitive information. By being mindful of access permissions, you can limit the data security risks of unauthorized access and potential data breaches.
2. Identify sensitive data and storage locations:
To effectively protect your CRM data, it’s essential to identify the most sensitive information and understand where it is stored. This enables you to focus your efforts on implementing robust security measures for the areas that require the highest level of protection. By gaining clarity on the location of sensitive data, you can build targeted defenses and reduce potential vulnerabilities. So what is the most sensitive data your sales team is handling? Is it the personal phone numbers and addresses of customers, is it sensitive contracts, or is it something else? Whatever it is, make sure it is stored securely and that only authorized personnel have access – and only when absolutely necessary!
Another phenomenon affecting data security is understanding data sprawl. As sales teams accumulate and generate more data, systems can become vulnerable if they lack visibility into where the data resides and how it’s protected. Ill-managed or unreviewed cloud services can transition into shadow IT highlights the increasing risk of accidental exposure or unauthorized access to critical information held within CRM systems.
3. Perform risk assessments:
No, this isn’t the sexiest or most exciting sales topic, but it’s these ones that set leaders apart from the losers. Regularly conducting risk assessments is crucial in understanding the level of exposure your CRM data may face. Identify the percentage of your company’s workforce that has access to critical data. If more than 10% of employees have access, it may increase the risk of unauthorized data exposure. By monitoring and managing access levels, you can mitigate potential threats and enhance data protection.
4. Detect suspicious behaviors:
An effective CRM system should have mechanisms in place to detect and signal suspicious behaviors. For instance, if a sales representative suddenly downloads a large chunk of data or exhibits unusual activity, managers should be alerted promptly. By leveraging software tools that provide behavior monitoring and anomaly detection, you can identify and investigate potential security breaches before they escalate.
5. Keep an eye out for phishing or scam attempts:
Phishing and scam attempts continue to be a significant threat to data security. It is crucial to remain vigilant and regularly monitor for phishing attempts targeting your employees. Educate your team about recognizing and reporting suspicious emails or messages. By staying proactive in combating such threats, you can prevent unauthorized access and data breaches.
6. Ensure secure connections:
When accessing your CRM system, it is vital to establish secure connections. Encourage your team to use Virtual Private Networks (VPNs), such as Cybernews-recommended ExpressVPN and NordVPN, or secure Wi-Fi networks when accessing CRM data remotely. By prioritizing secure connections, you minimize the risk of interception or unauthorized access to sensitive information.
7. Regularly update operating systems:
Keeping your operating systems up to date is a fundamental aspect of data security. Software updates often include critical security patches that address vulnerabilities. Regularly applying these updates to your CRM system and associated devices ensures you stay protected against the latest security threats.
8. Leverage effective password practices and Two-Factor Authentication:
Passwords serve as the first line of defense in protecting your CRM data. Encourage your team to adopt strong, unique passwords and regularly update them. Additionally, implementing two-factor authentication adds an extra layer of security by requiring a secondary verification method, such as a mobile code or biometric authentication. By leveraging these practices collectively, you enhance the overall security of your CRM system.
By following these guidelines and integrating them into your data protection strategy, you fortify your CRM against potential threats and reduce the risk of data breaches.
How to maintain adequate security using vendors/service providers/integrations
There are also critical aspects of maintaining robust security when utilizing vendors, service providers, and integrations within your CRM ecosystem. Ensuring that these third-party tools, plugins, and integrations align with your security requirements is essential to safeguarding your CRM data effectively.
Before you choose which third-parties to integrate with, first determine their security credibility by looking for certifications such as ISO 27001, which demonstrates a commitment to information security systems.
Next, check their reputation in the industry by considering recent reviews. Websites like CNET and other reputable platforms often provide insights into the reliability and security of various tools. Pay attention to feedback and experiences shared by other users to gauge the tool’s effectiveness and security track record.
A critical step in evaluating the security of third-party tools is researching their history for any past data breaches. Look into the vendor’s track record and check if they have experienced any major security incidents. This information can help you make informed decisions and assess the potential risks associated with integrating their services into your CRM system.
While privacy policies may be lengthy and often considered tedious to read, taking the time to thoroughly understand them is essential. Privacy policies outline how vendors handle and protect your data, providing valuable insights into their data security practices. Look for transparency, clear data handling procedures, and details on how they protect your information from unauthorized access.
Now you’ve done your research, you should be in a good position to choose a third-party vendor that you can trust. Remember, you’re not choosing this only on your own behalf but also on behalf of your customers. It’s absolutely critical that choosing this vendor isn’t going to impact the trust you have built with your clients.
Regulations and certifications that ensure data is protected
Whether you are looking for a new CRM, a tool to integrate, or a new chrome extension, there are two key things to look out for. ISO 27001 certifications and GDPR compliance provide valuable assurance that service providers prioritize the protection and secure handling of your CRM data.

Your data is safe with us
ISO 27001 Certification
ISO 27001 is an internationally recognized certification that sets specific requirements for managing and protecting information security. Service providers who obtain this certification demonstrate their commitment to implementing robust security controls and maintaining a comprehensive information security management system.
To achieve ISO 27001 certification, service providers undergo rigorous processes such as risk assessments, regular security checkups, and the establishment of frameworks for managing information security. This certification ensures that the vendor has established processes and practices in place to safeguard data confidentiality, integrity, and availability. Those practices are outlined in Annex A of ISO 27001, which contains 114 controls divided into 14 domains.
For customers, partnering with ISO 27001 certified service providers creates a sense of trust and reassurance. The certification serves as proof that the vendor adheres to global best practices in information security. It provides customers with the confidence that their data is handled securely and that the service provider is dedicated to maintaining the highest standards of data protection. Choosing ISO 27001 certified companies can be seen as a mark of reliability and helps establish a strong foundation of trust between the vendor and their clients.
Being ISO certified can also distinguish yourself from other competitors. In our case, Surfe is ISO 27001 certified – not many of our competitors are and this makes us by far the most trustworthy when it comes to data security.
GDPR Compliance as a Data Processor and Handler
The General Data Protection Regulation (GDPR) is a comprehensive data protection framework applicable to companies operating within the European Union (EU) or handling EU citizens’ personal data. It places significant emphasis on protecting individuals’ privacy rights and sets strict requirements for the processing and handling of personal data.
As a data processor or handler, knowing how to be GDPR compliant is crucial for third-party vendors and integrations. GDPR mandates that service providers adopt appropriate technical and organizational measures to ensure the security of personal data they process or handle on behalf of their clients. This includes implementing safeguards to prevent unauthorized access, disclosure, or loss of data. So it’s super important that you keep track of what customers opt-in to and opt-out of (remember this for your GDPR compliant email marketing campaigns), as well as their geographical specificities. A well-maintained and secure CRM will help you prepare for GDPR compliant prospection.
For customers, partnering with GDPR compliant vendors and integrations offers reassurance that their CRM data is handled in accordance with stringent data protection regulations. GDPR compliance establishes a framework that prioritizes the privacy and security of personal data, ensuring that the rights of individuals are respected and protected. When selecting third-party vendors, it is essential to verify their GDPR compliance and confirm that they adhere to the necessary data protection standards.
By considering ISO 27001 certification and GDPR compliance when evaluating third-party vendors and integrations, you can make informed decisions and select trusted partners who prioritize data security and privacy. These certifications provide tangible evidence of a vendor’s commitment to maintaining the highest security standards, allowing you to confidently integrate their services into your CRM ecosystem.

Ready to take your CRM data to the next level
Increase the accuracy of your data and improve the way in which you handle it with Surfe. Don’t rely on humans copy and pasting – Surfe will ensure the safe movement of your prospects data from LinkedIn to CRM and back with full reliability.